
I thought I understood Linux file permissions — but it turned out there were a few conceptual gaps. This topic, while not the most exciting, is quite important. So read on and see if you have a solid grasp.
Firstly, any file or directory in Linux has different categories of permissions — user, group, and other. The different permissions set for these groups determine who can do what with a given resource. If we inspect a file in our system we’ll see the following:

As you probably know, “-rw — rw-r — ” describes the permissions on the file “print_sq_pattern.c.” The “vagrant vagrant” section means that the files user is “vagrant” and the files group is “vagrant.”
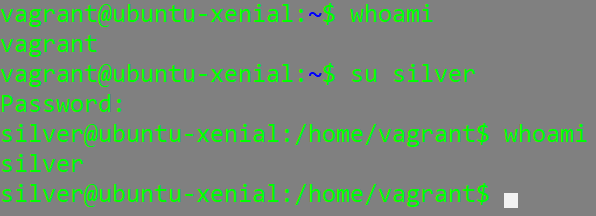
You can change the user on your system by typing “su” and then the users name:
You can examine the groups that your user belongs to by typing the command “groups”:

(the user silver belongs to the “silver” and “vagrant” groups)
If you execute the groups command with no arguments it will by default display all the groups that the currently logged in user belongs to:
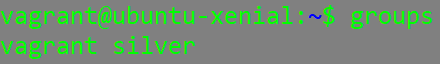
(the first group listed is always the users primary group)
You can also examine the groups that your user belongs to as well as the other users that belong to your group by examining the “/etc/group” file:

(the “tail” command here displays only the last 20 lines of the file)
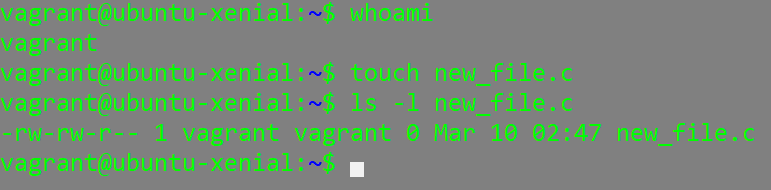
As you can see above, the user “silver” belongs to both the group silver and vagrant. Each user belongs to at least one group. When you create a new user, a group with that same name will be created by default. When you create a new file as that user, the file will belong to that users “primary group” by default.
Or you can see what groups any user on the system belongs to by typing members [group name]:

The “id” command prints the real and effective user and group id’s.
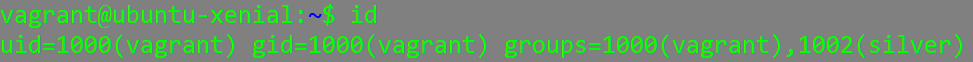
(we can also see the uid of the user silver)
Here’s one situation regarding executable files and permissions that confused me:
For example, if a certain file “print_sq_pattern.c” has the following permissions:
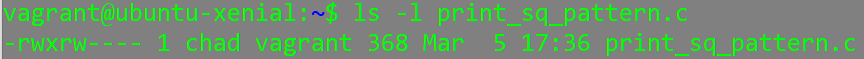
This says that no groups can execute the file and only the user “chad” can execute the file. However, if we log-in and attempt to execute the file (while logged in as the user “vagrant”) it appears we can:

We’re able to execute this program because the executable file “a.out,” has the following permissions and the owner of the file is vagrant:

If we want only the user (owner of the source code file) chad to be able to execute the file we should change the permissions of the binary file:

We also need to change the binary files owner to chad:
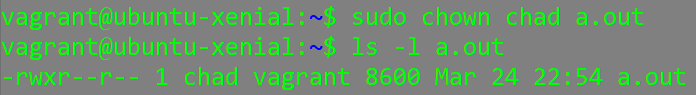
Now, if we try to execute the binary file while logged in as the user vagrant we will be unable to:

It seems that, by default, on this system:
binary files have the following permissions when they are created:
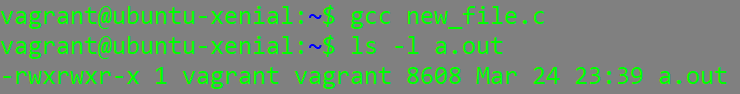
Hopefully this has increased your confidence with regards to linux permissions and how to view and change them on your system.

